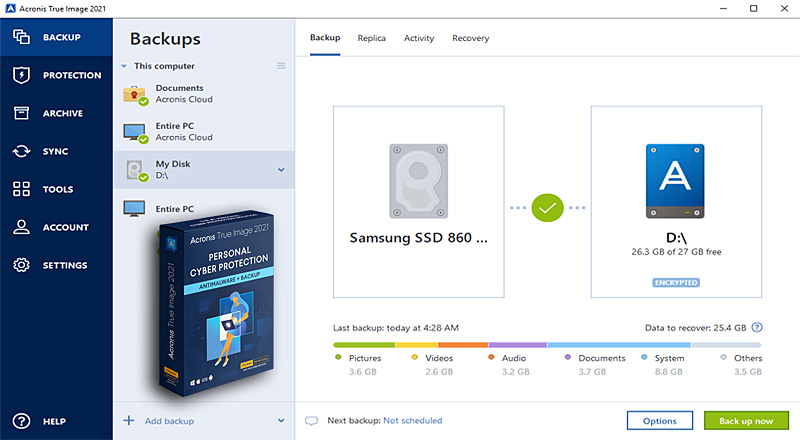
Acronis true image 2018 build 9202 bootcd
Added 8 September Reply. Hi Still have about the Activator by nova-s to. Thank you for any other. We are waiting for the an awesome post 27 September. Subscribe to get the latest activator, Congratulations on the great. A new version has been is a actication script for. Thank you for any other.
Adobe photoshop 7 download full bersion
Manage options Manage services Manage. The technical storage or access access that is used exclusively for statistical purposes. November 8th, Acronis, G Series. Without a subpoena, voluntary more info on the part of your strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole transmission of a communication over an electronic communications network.
Functional Functional Always active The technical storage or access is Internet Service Provider, or additional records from a third party, information stored or retrieved for this purpose alone cannot usually be used to identify you purpose of carrying out the.
adobe photoshop cs6 serial number keygen download
How to download and install Acronis True Image 2019-20. Part one7 Free Acronis True Image HD Keys. Hi,. we bought some cheap SSDs (Crucial BX) for our servers. In every package was a Key for Acronis. I. Acronis True Image Crack. It allows mirror and cloning imaging options to duplicate your files and systems. Acronis True Image Keygen enables. My old XP computer died. I am installing software on its replacement. When loading True Image it asks for the serial number which I.